With the world advancing to the digital age over the last decade, the consumption of data is increasing at an exponential rate. Data centers, which house a large group of networked computer systems and peripherals such as telecommunications and storage systems by various organizations for remote storage, have become hotbeds of sensitive and critical information for companies globally. It is thus natural for businesses to want to protect this information. Considering the number of data breaches that have occurred over the last couple of years an increasing number of corporations are turning to biometrics, and rightly so.
As per the study published in Forbes, 74% of data breaches occur due to credential abuse (i.e. passwords, PINs, card thefts). Customers who trust their data center partners with the security of their data expect and require world-class security.
Invixium biometric products are engineered with scalable technology to stand the test of time, including ample processing power and memory so that they can meet the challenges of tomorrow. As an added benefit, some products are designed to serve multiple purposes (like intercom and surveillance) allowing a reduction of the number of discrete devices required around the secured entry.
Here are some of the needs of data centers and how Invixium solutions meet these needs:

Biometric Access Control Security
As data center companies and their customers have become aware, even the most sophisticated card technologies have a fundamental flaw which is that a plastic access card can change hands far too easily with or without the knowledge of the card owner. Biometrics uses the technology that we are all born with to positively identify that the user of an access card is, in fact, the authorized user. In other words – “Biometrics is the only solution to prove that you are who you say you are”.
A more secure replacement to RFID card access for the entrance to the data center is via IXM TOUCH 2, which allows for up to 3-factor authentication via fingerprint, access card and/or PIN providing the perfect balance of security and convenience.
For the highest level of security, IXM TITAN allows for two biometric modes of authentication, facial recognition as the primary and fingerprint (or finger vein) as the secondary and furthermore can provide up to 4-factor authentication using a face, finger, access card, and/or PIN. IXM TITAN allows for the use of any combination of these 4 factors for areas within the facility that need higher or lower levels of security.
Intercom with Biometric Device
Various doors within a data center facility require an intercom, such as the main entrance where visitors might be buzzed into a reception area or within a mantrap where a user having difficulty might need to call the security desk. IXM TITAN and IXM TOUCH 2 support SIP protocols and intercom functionality, including bi-directional audio and DTMF, so that existing infrastructure can be used and two discrete devices can be combined into one attractive and compact device for access control as well as intercom.
The cutting-edge technologies and features available in the IXM TITAN also allow it to fully support HD resolution video intercom in addition to audio intercom. This is achieved using a SIP Client, when the TITAN and the receiving device (a tablet or a smartphone) are on the same Wi-Fi network. This further helps improve security in a location as the visitor face can be seen, before letting anyone into the premises.


Video intercom between the TITAN and a smartphone via W-Fi connectivity
Surveillance
With a 21.0MP camera incorporated into IXM TITAN, users may easily stream and record live, motion, and event-based video through the HDMI interface. The TITAN is able to provide a high-resolution IP video stream that can be viewed and recorded on virtually any Video Management platform.
TITAN video feed from the other side via HDMI.
Audit Trail
It is always a good idea to have an audit trail available for areas that are as sensitive as data centers, in case of a major security breach. Invixium solutions, in addition to providing security, also provide an audit trail of all personnel entering the restricted areas. Moreover, the Invixium software IXM WEB also keeps logs of all personnel who have logged into the system, changed user access rules or device settings, allowing the organizations to always know what the root cause was in case of a break in or a hack. Finally, this also helps to reduce insurance costs for data centers as it gives the insurance companies a certain level of confidence against data breaches due to user credential abuse.
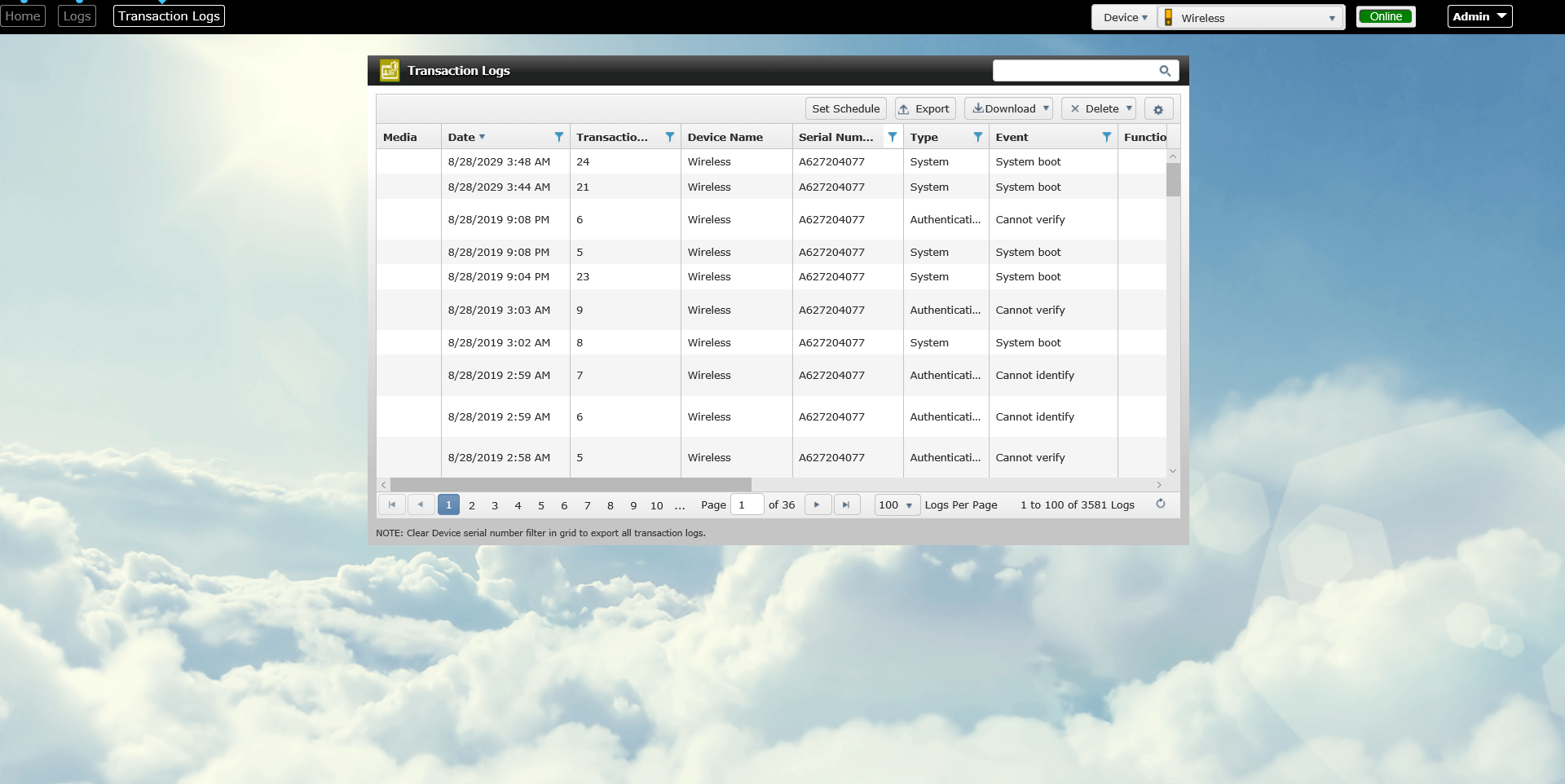
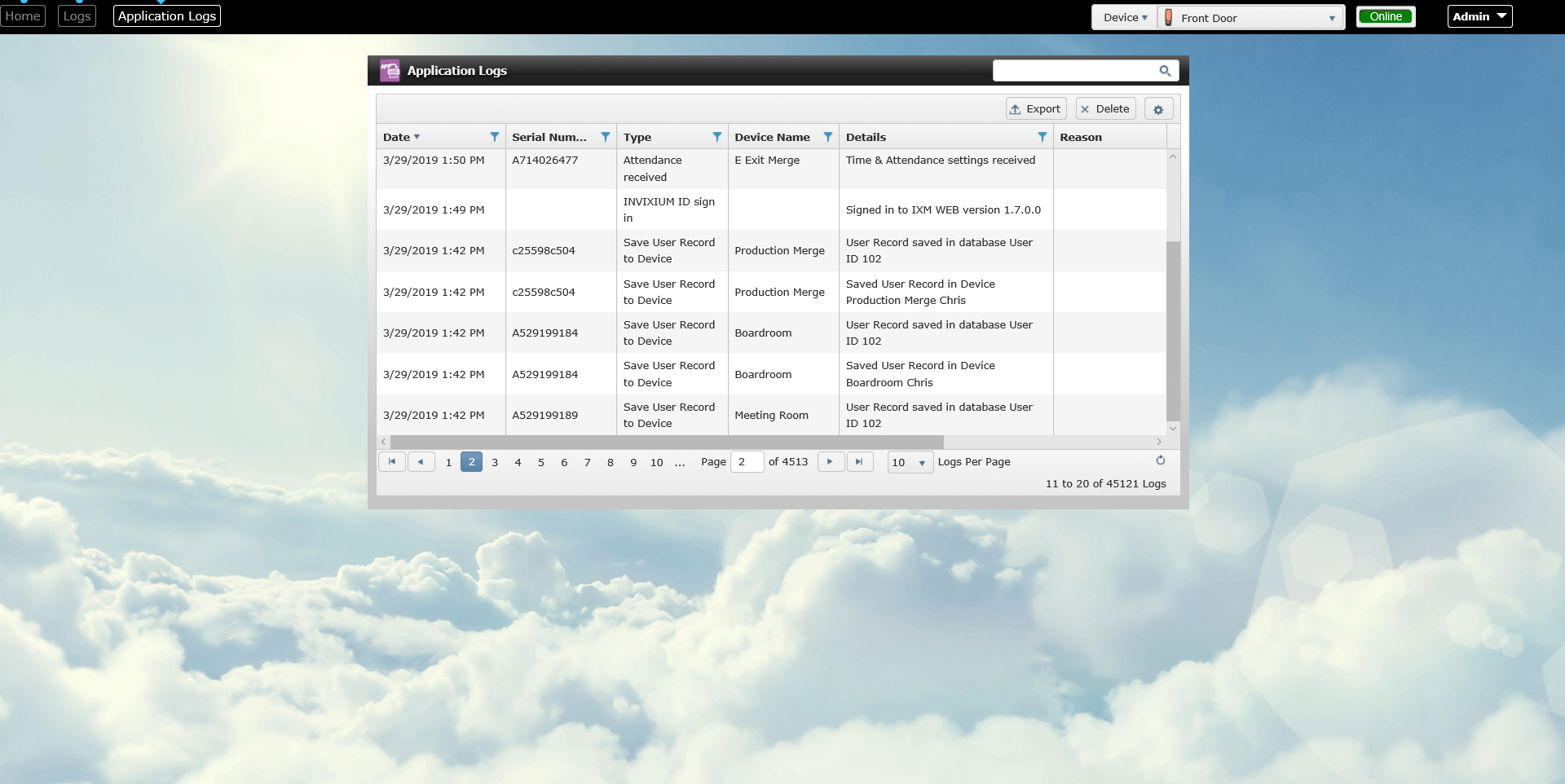
Transaction Logs and Application Logs in IXM WEB for Audit Trail purposes
Invixium offers a full range of biometric solutions that utilize modern technology by way of Android OS, capacitive touchscreen LCD interfaces, onboard processing and storage to deliver biometric solutions for access control, workforce management and smart building automation. Designed for ease-of-use and install, Invixium products provide security and convenience aimed to deliver ROI for data center business owners.
Have a project where IXM products would meet your requirements?
Contact us:
sales@invixium.com
For more information, visit:
invixium.com






